Implementing DevSecOps is crucial for organizations aiming to integrate security seamlessly into their software development lifecycle. Here’s a statistic that underscores its importance: the global DevSecOps market was valued at $3.73 billion in 2021 and is projected to soar to an impressive $41.66 billion by 2030, growing at an annual rate of over 30%. Why the surge? Because leaving security as an afterthought is costly.
Companies that have embraced DevSecOps see the payoff. They cut vulnerabilities by more than half, with only 22% of their apps left exposed compared to 50% in less-secure setups. Simply put, with DevSecOps practices your organization will protect your data and IP before the bad guys even get a chance.
And the cherry on top? Speed. DevSecOps secures your software as well as turbocharges delivery. GitLab’s recent survey showed that over half of organizations are now using DevOps or DevSecOps, up 9% from last year. Why? Faster delivery without compromising on security equals happy customers and healthier bottom lines.
Take HSBC, for example. By embedding security into their agile cloud transformation, they cut down on last-minute fire drills and showed their teams that security isn’t a blocker — it’s a business enabler. When security works with you, not against you, magic happens.
The takeaway? By embedding security practices from the outset, businesses can enhance their security posture and deliver reliable software efficiently. Let’s discover how to implement DevSecOps effectively and step by step
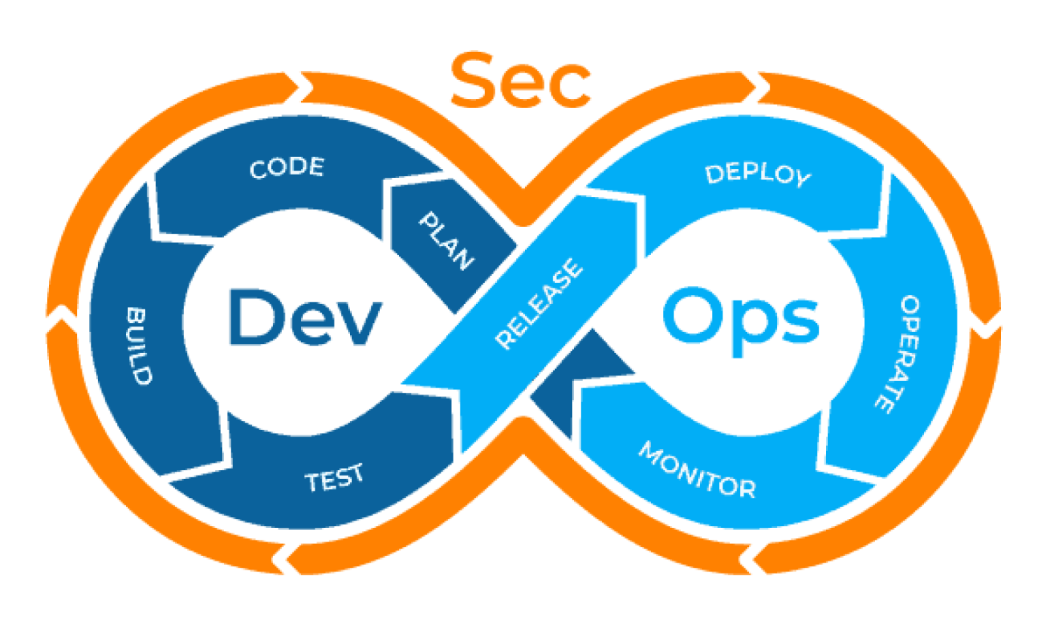
Step 1. Assessing Current Security Practices
Before integrating DevSecOps, you must understand your current security maturity. Begin by conducting a comprehensive evaluation of existing security measures, processes, and tools. This step identifies vulnerabilities, bottlenecks, and areas requiring improvement. It lays the groundwork for informed decision-making and resource allocation.
What It Brings:
- A clear understanding of risks in your software lifecycle.
- Prioritized roadmap for improvement based on critical weaknesses.
How to Do It:
- Conduct a security audit
Example: An e-commerce company realized that their checkout system was sending unencrypted payment data over the network. By auditing their processes, they implemented TLS encryption, protecting customer information and avoiding data breaches. - Map your workflows to compliance requirements to ensure regulatory adherence, avoiding fines and reputational harm.
Example: A healthcare provider used automated tools like Qualys to scan their systems for HIPAA compliance gaps, identifying insecure patient data storage in legacy systems. - Utilize tools like Rapid7 or Nessus to automate vulnerability detection and gain insights into your environment.
Step 2. Build a Cross-Functional Team
DevSecOps relies on collaboration across traditionally siloed teams (development, security, and operations). Without breaking silos, efforts to integrate security into workflows will fail. Firstly, define clear security objectives aligned with the organization’s vision. Next, engage stakeholders across development, operations, and security teams to ensure a shared commitment to these goals.
What It Brings:
- Shared responsibility for security rather than relying solely on a security team.
- Faster identification and mitigation of vulnerabilities.
How to Do It:
- Form a DevSecOps team. Include representatives from development, security, and operations.
Example: Netflix created security champions embedded within each dev team. This allowed developers to flag potential risks during the design phase instead of waiting until after deployment. - Clarify roles with a Responsibility Assignment Matrix (RACI). It’ll allow you to avoid task duplication and ensure accountability.
Example: For vulnerability management, developers fix code-level issues, security teams validate fixes, and operations deploy them. - Conduct regular meetings for collaboration and alignment. Use tools like Jira for tracking security tickets, Slack for communication.
Step 3. Provide Continuous Security Training
Your security is only as strong as your weakest link. Educate development and operations teams through targeted security training programs. Promoting security awareness fosters a culture of shared responsibility, ensuring that security considerations are integral to daily operations.
What It Brings:
- Reduced likelihood of introducing vulnerabilities due to ignorance.
- Empowered teams that prioritize secure coding and configurations.
How to Do It:
- Schedule regular training sessions. Focus on secure coding (e.g., preventing SQL injection, XSS).
Example: Amazon Web Services (AWS) mandates secure coding training for its engineers every year. It reduced their production bugs caused by security flaws by 30%. - Use gamification. Host Capture the Flag (CTF) competitions or gamified vulnerability hunts.
Example: A fintech startup created a CTF where teams exploited a mock payment app. It helped developers learn how attackers think. - Provide a knowledge base with tools like Confluence or Notion.
Step 4. Integrate Security into the CI/CD Pipeline
Traditional security checks occur at the end of development, making vulnerabilities costly to fix. Integrating security into CI/CD ensures issues are detected early when fixes are cheaper and faster. Also, incorporate security controls at each phase of the software development lifecycle. Utilize tools that facilitate secure code reviews, vulnerability scanning, and threat modeling to proactively address potential security issues.
What It Brings:
- Faster remediation of vulnerabilities.
- Reduced deployment delays due to late-stage security issues.
How to Do It:
- Automate static code analysis (SAST). For example, run SAST tools like SonarQube in your CI pipeline.
Example: At Capital One, SAST tools reduced high-severity code vulnerabilities by 50% in just six months. - Embed Dynamic Application Security Testing (DAST). Test running applications in staging environments.
Example: Shopify uses OWASP ZAP to simulate attacks on their apps before production, ensuring APIs resist unauthorized data access. - Enforce pre-deployment security gates. Set thresholds for vulnerabilities (e.g., “no critical issues”).
Tools: GitLab Security Scanning, Jenkins plugins.
Integrate Security Without Compromising Speed
Protect your software and accelerate delivery with Sphere’s expertise.
Step 5. Automate Security Testing
Why This Step Is Crucial:
Manual testing can’t keep up with modern DevOps speed. Automation ensures consistent and timely detection of security issues, reducing human error. For DevSecOps, automation includes static and dynamic analysis to provide continuous feedback. For organizations looking to implement DevSecOps seamlessly, Sphere Inc. offers tailored automation practices.
What It Brings:
- Scalability for large applications with frequent updates.
- Better ROI by reducing manual effort.
How to Do It:
- Implement SCA for open-source dependency checks with tools like Snyk or Black Duck.
Example: Uber detected and patched a vulnerability in their driver-routing service within hours using SCA tools, avoiding potential data leakage. - Combine SAST and DAST. Use tools like Fortify (SAST) and Burp Suite (DAST) together to cover all bases. They help to identify vulnerabilities during both code writing and runtime.
Step 6. Implement Continuous Monitoring and Incident Response
Modern threats evolve constantly. Continuous monitoring ensures vulnerabilities are detected in real time, and robust incident response minimizes downtime and damages. Develop clear incident response protocols to enable swift and effective mitigation of security breaches.
What It Brings:
- Proactive threat detection.
- Faster recovery from incidents, minimizing business impact.
How to Do It:
- Deploy real-time monitoring. Use tools like Splunk, Datadog, or Wazuh.
Example: LinkedIn’s anomaly detection system flagged suspicious API usage patterns, helping them mitigate a data scraping attempt. - Develop an Incident Response Plan. Define steps for containment, eradication, recovery, and communication.
Example: Slack’s response plan includes automated failover during DDoS attacks, ensuring uninterrupted service while mitigating threats.
Step 7. Foster Collaboration and Feedback
DevSecOps thrives on open communication and a culture of shared responsibility. Encourage collaboration between development, security, and operations teams. Regular meetings and shared tools facilitate communication, ensuring that security is a collective responsibility.
What It Brings:
- Faster resolution of vulnerabilities through collaboration.
- A culture of continuous improvement and shared accountability.
How to Do It:
- Establish cross-team feedback sessions:
Example: Atlassian’s engineering teams hold retrospective meetings after each sprint, discussing security tickets and bottlenecks. - Use shared dashboards for visibility with tools like Grafana or Kibana.
Example: Airbnb created a centralized dashboard to track security metrics, such as unpatched vulnerabilities, across teams.
Step 8. Continuously Improve Through Metrics
Why This Step Is Crucial:
Metrics provide a measurable way to track progress, identify gaps, and demonstrate the effectiveness of DevSecOps initiatives. Conduct periodic assessments to evaluate the effectiveness of DevSecOps practices. Continuous improvement is vital to adapt to emerging threats and evolving business needs.
What It Brings:
- Data-driven insights for better decision-making.
- Evidence of ROI for DevSecOps efforts.
How to Do It:
- Define key metrics:
- Time to Remediate (TTR).
- Percentage of automated security tests passing.
- Number of vulnerabilities detected in staging vs. production.
- Etc.
Secure, Streamlined, Scalable
Implement DevSecOps for safer, faster, and more efficient software delivery.
Recommended Tools for DevSecOps
- CI/CD Automation: GitLab CI/CD, Jenkins.
- Static Code Testing (SAST): SonarQube, Checkmarx.
- Dynamic Testing (DAST): OWASP ZAP, Burp Suite.
- SCA (Dependency Scanning): Snyk, Black Duck.
- Monitoring: Wazuh, Datadog, Splunk.
- Incident Response: PagerDuty, ServiceNow.
Staying Ahead of Security Challenges with Sphere
At Sphere, we understand the complexities of modern security challenges and have designed our DevSecOps services to empower organizations at every stage of their security journey. We start with a meticulous assessment of your current security framework, identifying gaps and tailoring solutions that align with your specific needs. From there, we seamlessly integrate advanced security tools into your development pipelines, automating testing processes to ensure vulnerabilities are detected and resolved without delay.
We believe that technology alone isn’t enough. That’s why we prioritize training and support to equip your teams with the skills and resources they need for sustained success. Our AI-powered security solutions leverage machine learning to detect and respond to threats in real-time, providing an added layer of protection.
Our approach emphasizes shift-left security, which focuses on identifying and addressing vulnerabilities earlier in the software development lifecycle, saving time and resources while enhancing overall security. For environments requiring strict identity verification, we implement Zero Trust models, ensuring that only authenticated users and devices gain access. We also address the complexities of containerized environments, offering robust security solutions for Kubernetes and Docker, safeguarding your applications at every layer.
Contact us today to explore how our DevSecOps services can elevate your development pipeline.
Frequently Asked Questions
Subscribe for news updates!





